Higher education institutions are experiencing an increase in the number of cyber attacks targeting systems and individuals with access to sensitive data. Penn Office of Information Security (OIS) is noticing more sophisticated social engineering and phishing attacks aimed to steal personal data, valuable intellectual property, and financial data. OIS compiled six security tips to guide you to protect your information and Penn's sensitive data.
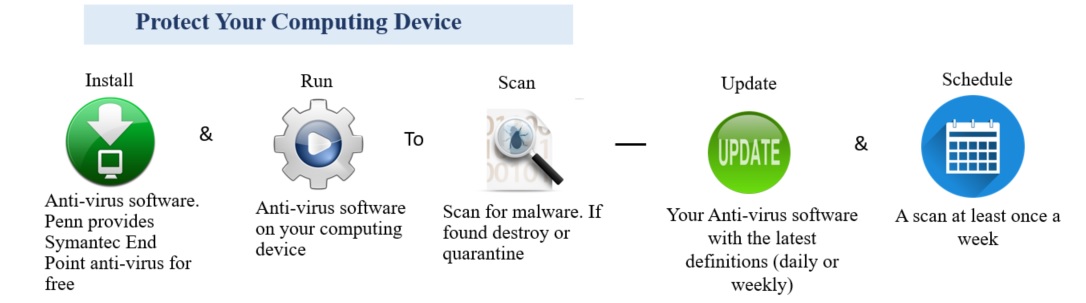
One of the common reasons for vulnerable devices is the lack of or expired anti-virus software. A virus is one of the Malware categories; a malicious code hidden in an email or text message link, attachment, pop-up window or online adds. Once executed, a virus may:
- Slow the performance of your computer
- Damage your computing device and systems
- Access other computing devices connected to the same network
- Grant hackers access to your confidential information and to any sensitive data you handle
- Carry another malicious code
- Send out unauthorized messages from your computer or email account
- Populate pop-ups to paralyze or slow down your computer
- Use your computing device as a host to attack other devices
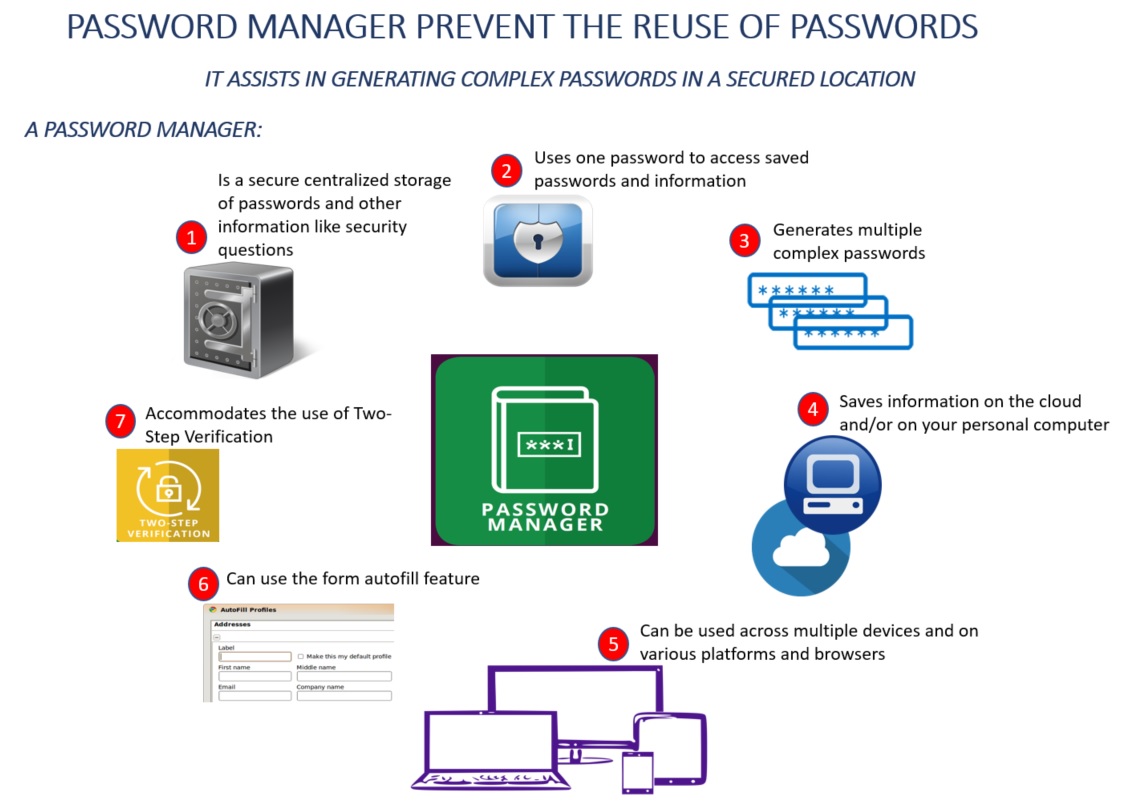
If you are struggling with creating and remembering complex passwords for all your online accounts use a password manager similar to LastPass.
With a password manager, you can:
- Have only one password to remember
- Create random complex passwords
- Save sensitive information in an encrypted format
- Have fast access to your accounts
- Manage shared accounts
- Meet the recommended password guidelines including PennKey password rules, using letters (capital and small), numbers and symbols
- Access your passwords using your Penn and/or personal email address
- Automatically back up and sync your passwords across all your desktop and mobile platforms.
Avoid trusting everything you see or read online. Verify information before you act.
Understand ...
- Social Engineering
It refers to techniques used by malicious individuals to manipulate users into sharing confidential information. Social Engineering comes in various forms, mentioning four:
-
Phishing Email - crafted with a sense of urgency to lure the recipient to take immediate action, e.g. click on a link, open an attachment or provide sensitive information. If you don't know the sender and is not expecting this email, report it to your department's IT support provider.
-
Phone Scam - A phone call requesting an individual to verify their bank account and/or PIN, or a username and password. The caller may provide partial information to gain the individual's trust. Financial institutions, government entities, and Penn do not ask for your sensitive information over the phone. Ask for a call back number and name, then report the incident to your department's IT support provider.
-
USB Flash Drive - An infected USB flash drive is left in a place easily found by others. The victim inserts this flash drive in their computer which results in the installation of malware. Avoid inserting such USB drives into your computer, instead, give the USB to your department's IT support provider.
-
Impersonation - A person pretending to be a technician or delivery personnel asking for your information or username and password. Ask for the technician or delivery personnel contact information and/or Penn ID to verify the person is legitimate.
- Penn Data Risk Classification
Penn classified its data into three categories based on the level of data sensitivity
High - Moderate - Low
- How to Protect Penn's Data
-
Use strong passwords and use a password manager, e.g. LastPass
-
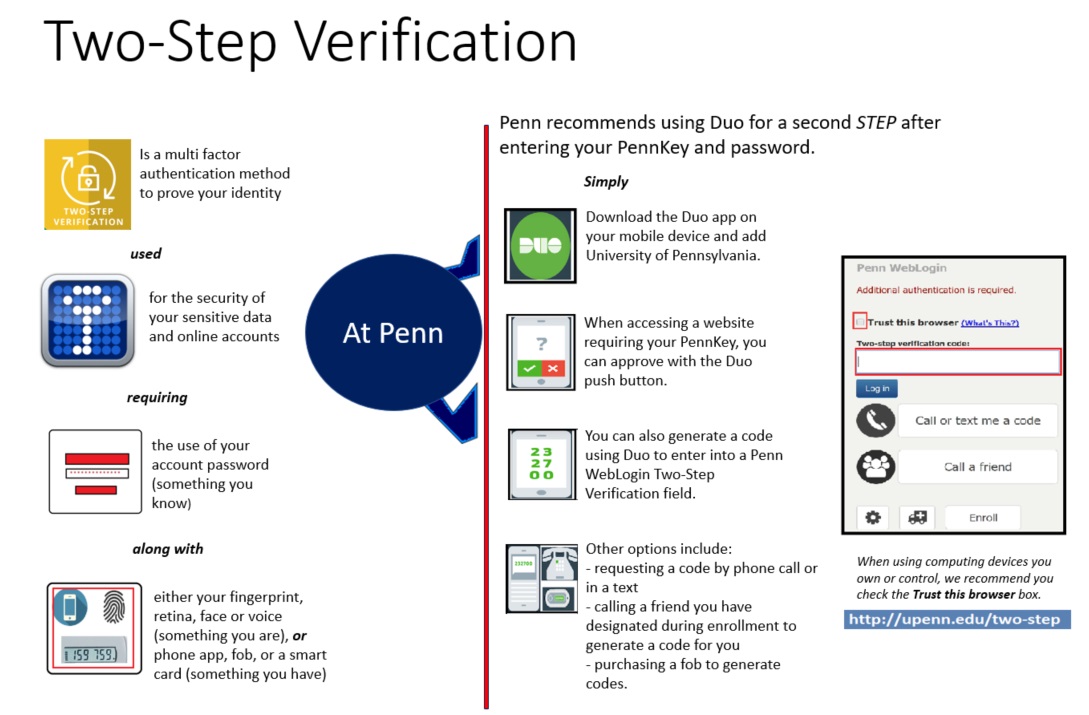
Enroll in Two-Step Verification
-
Store data in a secure location, e.g. Box
-
Use Secure Share to exchange sensitive data
-
Adhere to Penn Computing Policies and Guidelines
-
Take the Information Security Essentials online training
Verify ...
- Email Security
-
Despite its ubiquity, email is actually quite insecure
-
It is easy to forge the "from:' header, making it appear as if an email came from someone other than the sender
-
Most email messages can be easily intercepted, so don't use email for highly sensitive matters
-
Never include sensitive information such as SSNs in email or email attachments
- Online Information
-
Accuracy - Check at least three credible resources for information accuracy
-
Verify the legitimacy of the web address (URL) you intend to visit, e.g. www.upenn.edu is a Penn URL, whereas, www.upenn.org is not a Penn URL
-
Web adds may carry malware which may execute when you hover over the add or click on it. Avoid clicking on the web adds flashing on your screen
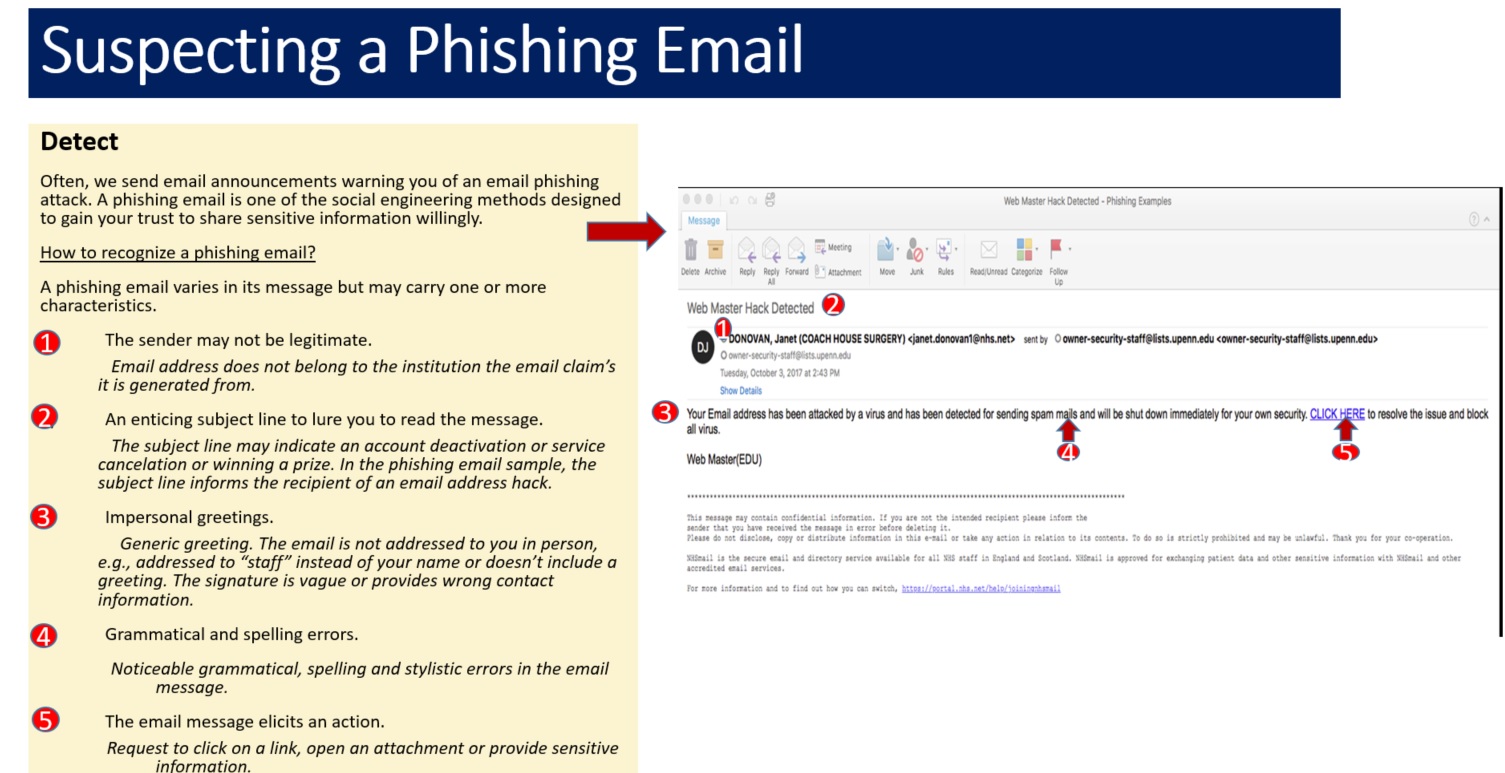
Phishing ...
- Pay attention to
-
Unexpected email
-
Message requiring immediate action
-
Unknown Sender
-
Fake sender email address
-
Spelling and grammar mistakes
-
How the sender is addressing you
-
Email signature
-
Fake or no contact information
- Protect yourself and Penn
-
Avoid clicking on email links and attachments
-
Hover over embedded email links to verify its origin
-
Be aware - Legitimate entities don't ask for your username and password in an email
-
Keep your computer and software up to date
-
Report suspected email and your stolen or lost computer to your IT support staff (LSP)
Patching your computing device software is one of the most critical steps to protect your computing device and sensitive information from unauthorized access. A patch is a software update to fix a software bug or security vulnerability. It can:
- Add new features to your device and remove outdated ones.
- Prevent hackers from exploiting your software weakness to steal data saved on your device or to gain control over your files.
- Enhance the performance of your software.
- Protect devices connected to the same network against threats.
- Allow access to information when needed without fear of loss or corruption.
If you have questions about patches and running software updates, please contact your IT support provider.